Still purchasing tools for network management,
traffic analysis, and log separately?
Still spending lots of time and effort doing network management
even with all the tools?
N-Reporter Combines Management and Analysis
in One Platform
N-Reporter differs from other reporters. It can collect, store and analyze Syslog/Flow data for query and report making; moreover, it correlates L3/L4 packet/byte from Flow with L7 events from Syslog. Also, N-Reporter supports Syslog from different brands and devices. It normalizes complex, long Syslog data and put them in a tidy form; IT administrators can know completely about every detail in Home network. What is more, N-Reporter is with AI analysis and auto-learning. It builds baseline automatically and sends real-time alerts; users do not have to set each threshold value manually and can make various reports with the analysis function. N-Reporter meets organizations’ needs for management, analysis, and audit, making IT operation much simpler and more effective.
Short Searching Process, Showing Full History Record
Tests in real environments show that N-Reporter can collect up to 20,000 Syslog data per second without dropping.ID Your Intranet: Smarter IT, Sorted Ips
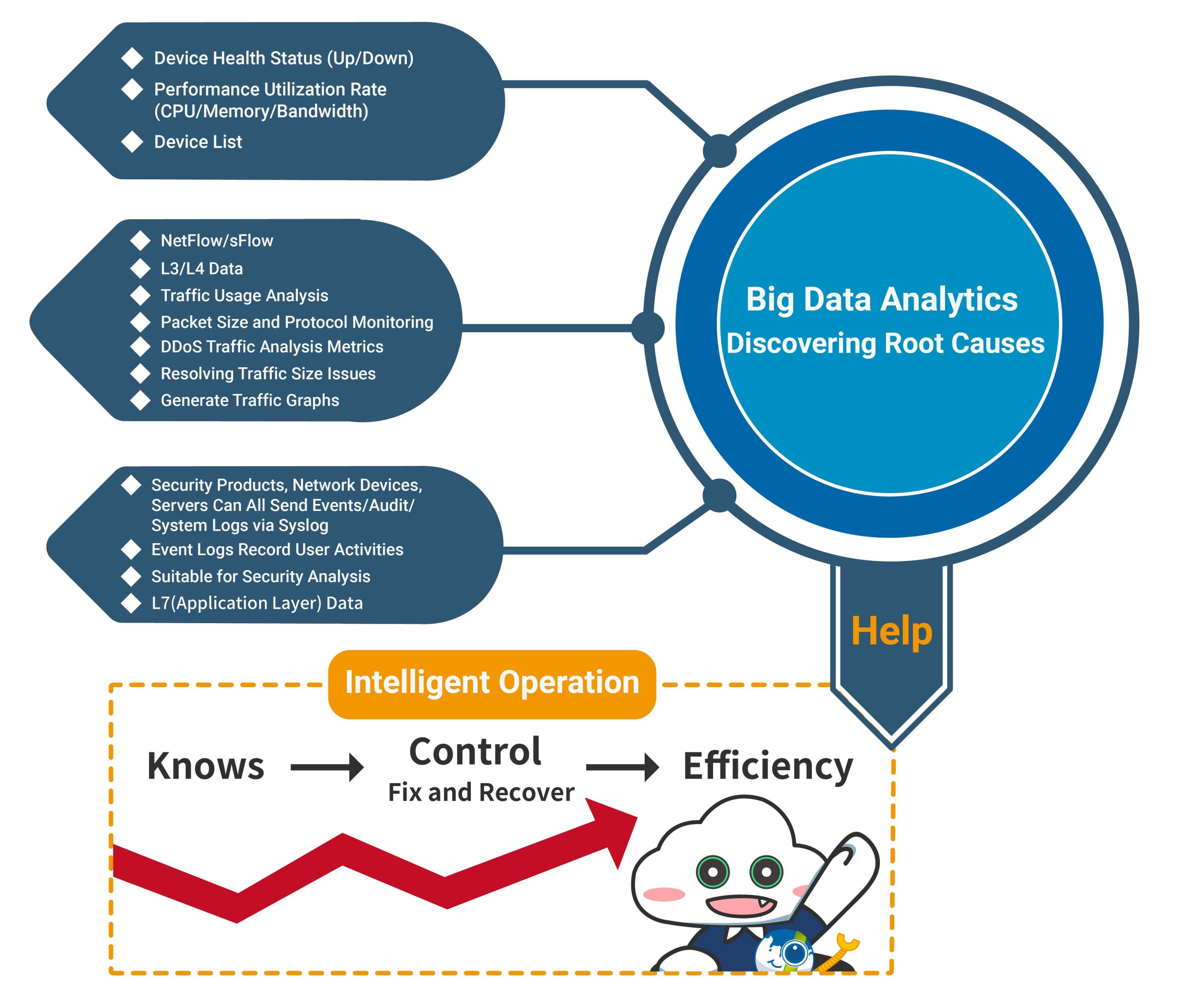
By utilizing multidimensional network management protocols and integrating operational data, N-Reporter provides IT managers with a comprehensive overview of the intranet. With Intranet IP ID, we could offer clear insights into users, actions, time, location, and devices, revolutionizing management perspectives. In case of anomalies or attacks, quick identification of the IP user and their physical location enables immediate intervention through unified defense mechanisms, preventing disasters from escalating. This approach ensures comprehensive and efficient network and cybersecurity operations.
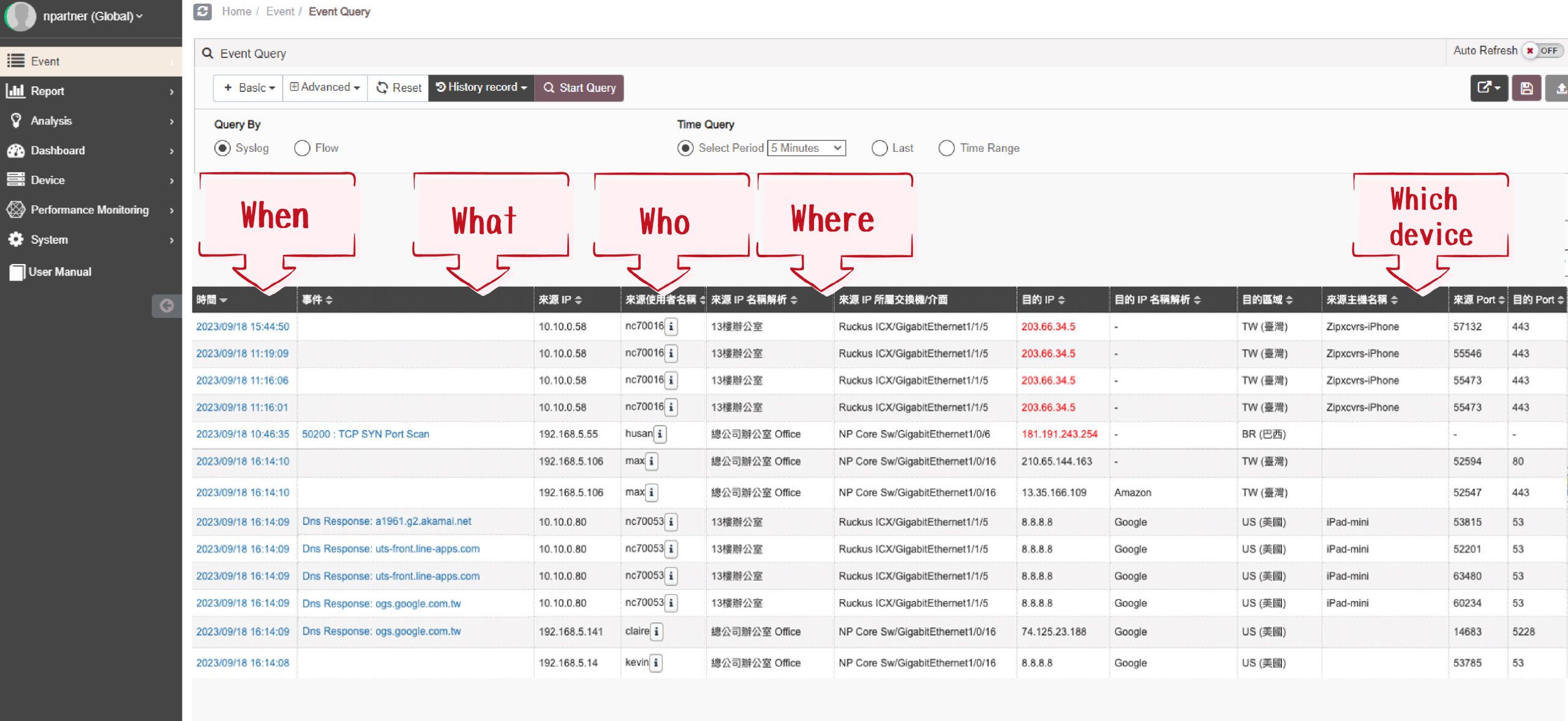
AI Forecast—Advanced Data Range Alerting
Our system employs AI to learn and define reasonable data range models for different network environments, eliminating manual threshold settings. It proactively alerts administrators when data surpasses acceptable ranges, often indicating abnormal usage or network attacks. Furthermore, it forecasts future trends based on historical data, facilitating proactive capacity planning to avoid last-minute expansions and associated budget and time pressures.
Collaborative Defense Solves Anomaly in 3-5 Minutes
N-Reporter’s powerful data analysis technology can detect anomalies in real-time and identify problem areas. Unlike other network management tools, it can integrate with third-party, cross-brand network devices such as switches, IPS (Intrusion Prevention Systems), and firewalls to create a “collaborative defense mechanism.” When abnormal behavior occurs, the system quickly analyzes and identifies the root cause. Managers can issue “block” commands directly within the system, eliminating the need to log into separate defense equipment, thus reducing response time. Additionally, “Action Script” function can be set to automatically block malicious attacks, minimizing manual response time and preventing the spread of viruses within the internal network.

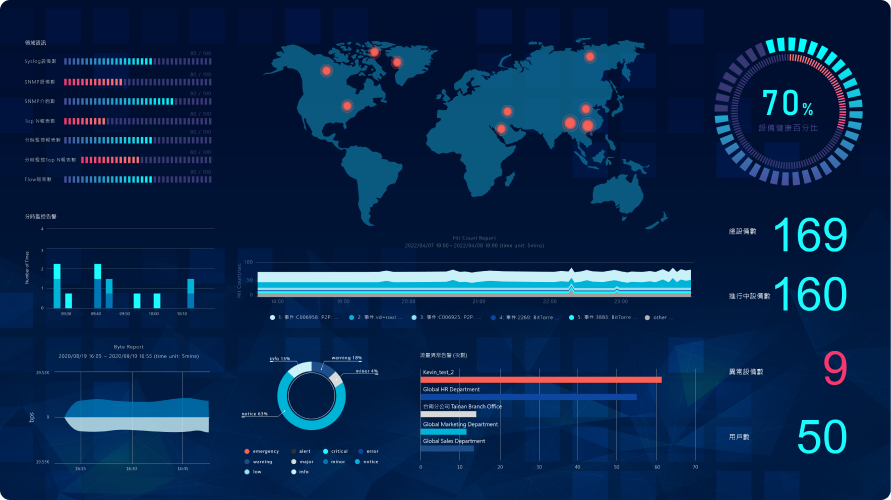
Intuitive UI - NOC+SOC: Real-Time War Room
- Do operation and management in web interface, with great convenience and simplicity.
- Various and real-time analysis, 24/7 continuous monitoring.
- We offer over a dozen default maintenance dashboards and theme templates to simplify setup, making it easier for users to construct their own customized security war room tailored to their environment.
Cut Off Malicious IPs, Stay Ahead with Rich, Real-time Data
Accessing threat intelligence for businesses isn’t easy or cheap due to high technical barriers and costly subscriptions, often from foreign providers. However, our system, N-Reporter, offers a solution. By collaborating with domestic research institutions, we integrate diverse threat intel sources (including our own) for rich, real-time data. Upon detection of malicious IPs or domains, our system immediately deploys a collaborative defense mechanism, distributing blacklists to defense devices to block threats at the source, ensuring proactive protection.
Conform to Audit Regulations
N-Reporter conforms to the internationally recognized encryption standard, FIPS 140-2, SHA2-256, SHA2-512 and AES, ensuring integrity and nonrepudiation of the data.